The End of an Era in Kubernetes NetworkingThe Kubernetes community has officially announced the reti...
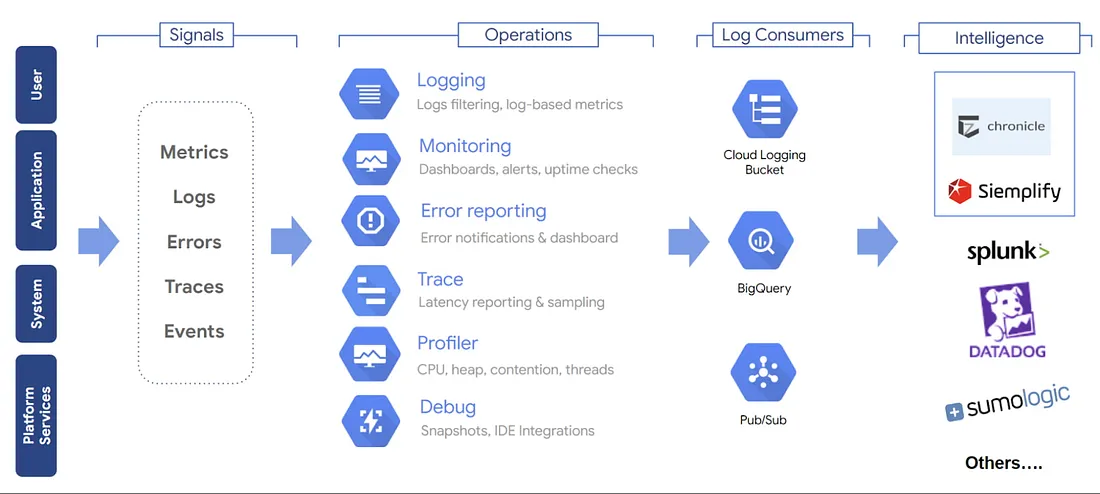
Hands-On Guide to Docker Observability in GCP
In modern cloud-native environments, the era of siloed metrics and logs is fading. What’s essential ...
Scattered Spider: What You Need to Know
Scattered Spider is not your average cybercrime group. With tactics that blur the line between tradi...
Build AI-Ready APIs: The Best MCP Tools for Developers
Model Context Protocol (MCP) has emerged as one of the most transformative developments in AI t...
How Comprehensive API Documentation Enhances API Security
Clear Understanding of FunctionalityDocumentation allows both development and security teams to focu...
Business Process Mapping Techniques and Methods
Just as navigators use maps to traverse vast seas, businesses can use process maps to analyse and na...
Strategies to Improve Services Maturity in Your Organization
Benchmarking the maturity of a Services function is closely linked with achieving success. When an o...
DevOps Pipeline: Fundamental Concepts & Phases
In today’s business landscape, accelerating the pace of software development is essential for ...
Essential Components of an IT Audit
The essential components of an IT audit Typically, IT audits are overseen by an organization’s...